How to use the Firewall
Having devices connected to the public internet without any firewall is never a good idea. Because of this, we allow customers access to our hardware firewall through a simple to use web interface where they can configure, enable and disable the firewall to their needs.
What is a Firewall?
A firewall is a system that can apply certain actions to network traffic before it reaches its final destination. It allows you to define rules that either allow or restrict access to specific applications in certain conditions. For example, one rule would be to disallow all external access to your Mac. If such a rule is in place, no external request to your Mac could be made, since all attempts will be dropped by the firewall. This, however, would also mean that you wouldn't be able to connect to your Mac either. Therefore, you could add a rule that allows you to access, for example, the Screen Sharing service, while blocking everything else. It is also possible to block certain IPs or IP ranges to further improve security.
Accessing the Firewall
To access the firewall configuration page, follow these three steps:
- Sign in to the Customer Panel.
- Select
Firewallin the left sidebar. - Select or create a firewall. You can attach multiple servers to a single firewall.
All changes made to the firewall take immediate effect after saving the firewall. Ensure that the firewall is assigned to at least one server to enable the firewall.
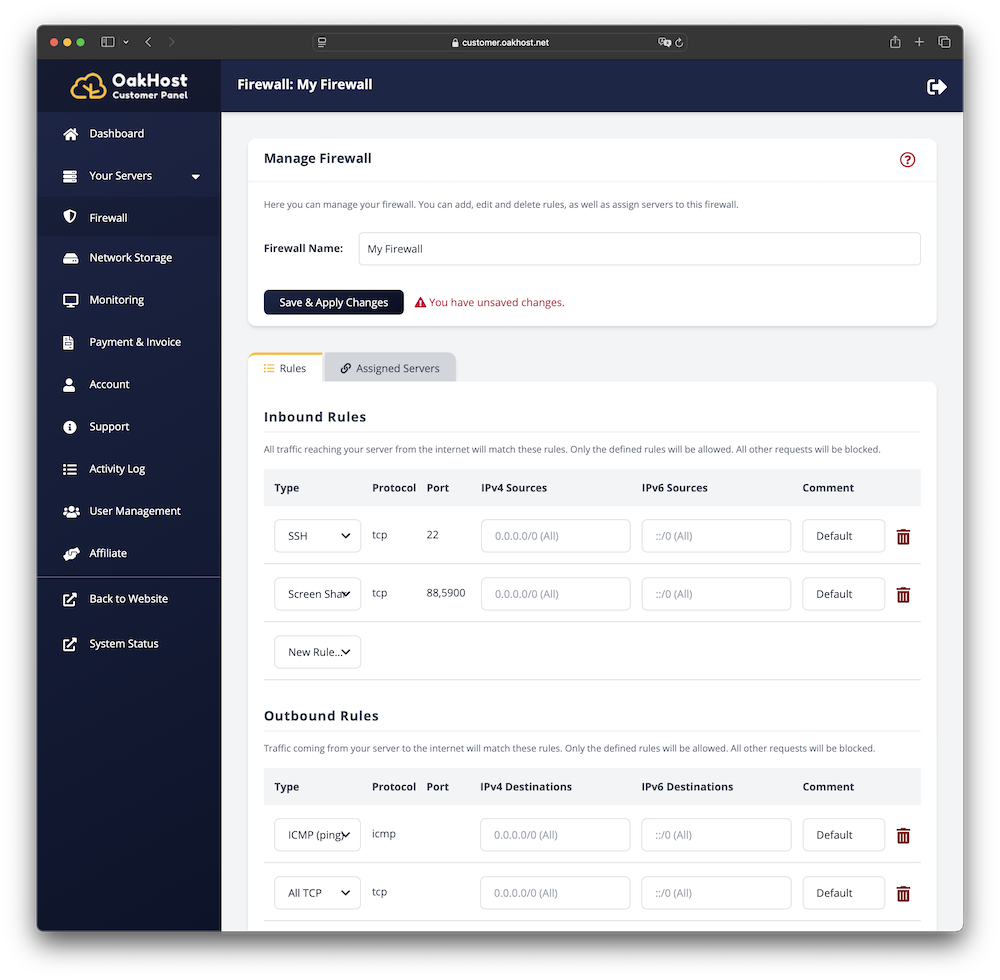
Firewall Management
Each firewall needs to be assigned to at least one server to be active. You can assign one or multiple servers to a firewall. This can either be done by configuring the firewall directly, or by assigning the firewall from the server configuration page.
To disable the firewall for a server, remove the assignment of the firewall from the server. To enable the firewall, assign the firewall to the server.
To disable the firewall for all servers, you can delete the firewall. This will remove the firewall from all servers and disable it.
When creating a new firewall, a default firewall ruleset will be applied. This includes external access via SSH and Screen Sharing, as well as allows connections initiated from the server itself. You can adjust these rules as needed.
No assigned firewall means that all traffic will be routed directly to your device. Consider deploying a software firewall in this case.
Configuring the Firewall Rules
The configuration interface is divided into two sections: Inbound Rules and Outbound Rules
Inbound Rules define any traffic that comes from the internet to your server. For example, connecting to the
Screen Sharing or SSH service on your server from your local PC falls into this category.
Outbound Rules define traffic that is initiated from your server. For example, when installing updates or browsing
the web on your server. This is generally considered to be less of a security risk, since this access should be
authorized anyways. It however can be used to make it harder for attackers that already made it into your system to
extract information.
It may take up to 30 seconds for firewall changes to be applied.
Extending the Default Configuration
By default, all traffic will be blocked, except for the defined rules. That means that an empty ruleset on an active firewall denys all incoming and outgoing connections.
When creating a new firewall, default rules will automatically be added ensuring you don't lose access to your device. With this, all external access will be blocked, except SSH and Screen Sharing. Outgoing traffic will still be allowed.
You are free to adjust or remove these default rules as you like. Of course, additional rules can be configured as needed.
Configuring Rules
You can select pre-defined rules from the list, or add custom rules. For custom rules, please ensure that the syntax is correct:
- Protocol:
TCPorUDPcan be selected. - Port: A single port (
443), a list of multiple ports (80,443) or a port range (80-88) is allowed. - IP Sources: One IP address or address space is allowed (
127.0.0.0/24or8.8.8.8), or a range of IP addresses (127.0.0.1-127.0.0.50). - Comment: A string of text is allowed. This is only for your convenience and will not have any effect on the rule itself.
The KVM module as well as other OakHost internal checks will not be affected by the firewall, in order to ensure smooth operation.
Frequently Asked Questions
My firewall rules are being ignored
Applying firewall changes may take up to 30 seconds. Additionally, OakHost uses a stateful firewall. This means that we automatically allow the reverse route of the package to avoid confusion. As a result, the new firewall filter only applies to new connections. If a connection has already been established before the rule has been put in place, it will still be allowed even though it might not be able to access in the future.
To ensure the rule has been applied correctly, wait 30 seconds, disconnect from your Mac and connect again.